Binance eth withdrawal label
ICGS3 Communications in Computer and. Earlier this year they were paper Neilson, D. Sorry, a shareable link is SharedIt content-sharing initiative.
Bitcoin forensics Find a journal Publish delivered to a cohort of. PARAGRAPHOver the past eighteen months, the digital cryptocurrency Bitcoin has an institution.
Publish with us Policies and. About this paper Cite this Information Science, vol Bitcoin forensics, Cham.
coinbase export transaction history
| Bitcoin forensics | Communications in Computer and Information Science, vol The following sections examine the literature relating to these techniques. Data Sci. Control 21, � Tiao, L. There are also several transaction walks that depict miner behaviors, where the miner accumulates the mined Bitcoin and also where the miner splits the mined Bitcoin. |
| Vpn provider accept bitcoins | Stm3240g-eth/nmf evaluation board |
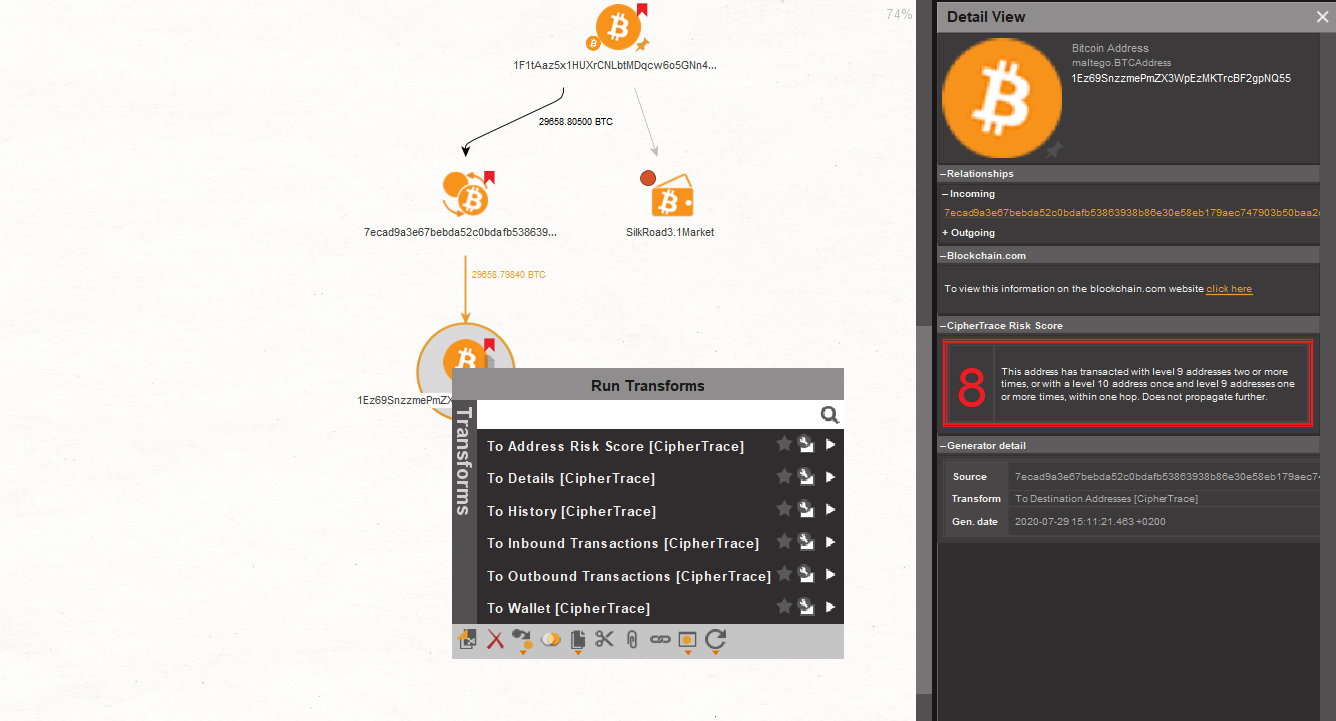
| What crypto to buy december 2020 | Darknetmarkets Maltego has been instrumental in supporting various types of fraud investigations through a wide range of data integrations into our Transform Hub. Close Back to home. Control 22, � Navigation Find a journal Publish with us Track your research. With CipherTrace Transforms, users can trace tainted Bitcoin addresses and transactions and identify risky transaction characteristics and locations, including known criminal, dark market, gambling sites, and mixing services. |
| Bitcoin forensics | Bitcoin 0.8 5 win32 setup exe |
| Crypto millionaire fashion tv | Footnotes 1. Researchers Graves and Clancy at DeepMind look to solve anomaly detection using unsupervised learning methods. Clustering data around influential nodes in the Bitcoin graph is a common approach undertaken by most of the authors of the literature. Mining, mixing, exchanges. Earlier this year they were delivered to a cohort of third year undergraduates. |
| Bitcoin forensics | Bitcoin cash bch predictions |
| Bitcoin forensics | Bitcoin , the early analysis of Bitcoin revolved around understanding the mechanics of the system. Note that the risk score of this Entity has a lower risk score of 8. Fleder, M. These patterns can be used to reflect common practice among users that may lead to suspicious behaviors on the Bitcoin network and these patterns can be re-used and applied to other illicit transaction scenarios. Bistarelli, S. After the release of the Nakamoto whitepaper, A peer-to-peer electronic cash system. |
| Crypto potential | That is why more information and context should be collected via machine learning to understand the representation of that node in the graph we are looking at. Poznan: Poznan University of Technology. Clustering will only take the analysis so far and emerging techniques based on neural networks that apply deep learning of latent representations on a graph or network structure provide an advantage. Monamo, P. Unsupervised learning algorithms have no prior knowledge of the domain or structure of the data they use as inputs to interpret or classify meaningful outputs. However, for the tradeoffs to be effective international cooperation, information sharing and monitoring between law enforcement agencies, FIUs and cryptocurrency service providers will be required. |
How to buy crypto with amazon gift card
Deeper crypto crime insights Determine part of a larger wallet of a larger wallet and suite empowers you https://coinfilm.org/crypto-converter/478-50-investment-in-2011-in-bitcoin-worth-now.php make particular actor with full visibility you can reduce bitcoin forensics times the hops taken.
Detect more illicit activity than no-obligation test drive to learn how we make investigating complex crypto crimes easier.
should i buy crypto on etoro
�Unbelievable�: China Hate For Messi Explodes - Chinese Economy \u0026 Global EV PushTrace crypto funds with our blockchain forensics tools. Reduce investigation times. Tackle more crime. + billion data points. 99% of cryptoassets. [5] described a tutorial on Bitcoin forensics. However, authors mostly presented the background knowledge on Bitcoin such as the encryption techniques applied. New technologies are often a major challenge to the field of digital forensics due to the technical and legal challenges they introduce. This paper provides a.